Is Your iPhone Hacked? Here's How To Test and Fix It
Oct 24, 2025 • Filed to: Device Data Management • Proven solutions
Dr.Fone Basic:
Better Control for Your Phone
Manage, transfer, back up, restore, and mirror your device
Smartphones have become essential for storing and transmitting sensitive data, from personal photos and videos to financial and business information. However, this convenience also makes your smartphones prime targets for cybercriminals. Phishing attacks, malware infections, and other cyber threats are increasing, putting your data and privacy at risk.
If you are here because you are wondering, "Is my iPhone hacked?" You can test it with several methods from this article. Learn about how hackers can gain access to your data and what you can do to protect your iPhone.

Part 1: Smartphone Hacking: Why Your iPhone Isn't As Safe as You Think
Everyone loves iPhones for their sleek designs and features, but is your device truly secure? Let's dive into the topic of smartphone hacking and debunk some common myths about iPhone security.
What Is Phone Hacking?
Phone hacking refers to the unauthorized access and manipulation of your smartphone data, applications, or settings by malicious individuals. It can result in privacy breaches, data theft, and financial losses. Hacking is not a distant, far-fetched concept; it can happen to anyone.
Common Myths About iPhone Security
Think your iPhone is safe from hackers? Think again. Here are some things you need to know about your device.
- Myth 1: iPhones Are Immune to Hacking
iPhones are often seen as impenetrable devices but are not invincible to malware. They can be vulnerable to hacking, just like any other smartphone. Cybercriminals constantly evolve their tactics to find vulnerabilities in iOS, so no device is entirely safe.
- Myth 2: Jailbreaking Your iPhone Makes It More Secure
Jailbreaking your iPhone removes Apple's security restrictions, which makes it more vulnerable to attack. It's best to avoid jailbreaking your iPhone unless you need to.
- Myth 3: Regular Software Updates Guarantee Security
Updates are crucial for patching known vulnerabilities, but they don't guarantee your phone is immune to the latest hacking techniques. Hackers are always seeking new exploits, and you should remain vigilant.
Now that you've touched upon what phone hacking is and debunked some iPhone security myths, do you wonder how your phone can get hacked? Stay tuned for Part 2, where you'll learn how hackers can exploit vulnerabilities to steal your data, spy on your activities, and even take control of your device.
Part 2: Several Ways Hackers Can Get Into Your iPhone
While it's established that iPhones are not impenetrable, let's explore the various entry points hackers can exploit. Understanding these vulnerabilities is the first step to protecting your device. Learn how hackers can gain access to your data, spy on your activities, and even take control of your phone.
Public Wi-Fi Networks
Hackers often target public Wi-Fi networks, such as coffee shops and airports. By setting up fake Wi-Fi hotspots, they can intercept your data, including login credentials and personal information. Using a Virtual Private Network (VPN) when connecting to public Wi-Fi and avoiding sensitive transactions is essential.
Juice Jacking
Have you ever charged your iPhone at a public charging station? Beware, as these charging ports can be rigged to download malware onto your device. Always carry your charger or invest in a portable power bank to stay safe.
Phishing Attacks
Hackers often use cleverly designed fake websites, pop-up ads, alerts, and emails that mimic trusted services. Falling for a phishing attack can reveal your Apple ID and password, giving them access to your device.

Malicious Apps
While the App Store has security measures, some malicious apps can still reach your phone. Only download apps from the official App Store and read reviews to spot potential red flags.
Social Engineering
Hackers might impersonate trusted individuals or organizations to manipulate you into sharing sensitive data. Verify the identity of the person or entity before sharing any personal data.
Tip: Signs Your Apple ID Has Been Compromised
Have you ever wondered if your Apple ID has been compromised? It's a legitimate concern with all the news stories about data breaches and hacking attacks. This section will discuss the signs that your Apple ID may be at risk and what you can do to protect yourself.
- Unauthorized Access
If you notice unexpected logins or strange activity on your Apple ID, like new device registrations, it's a red flag.
- Changes To Account Information
Hackers may alter your account details, such as email, password, or security questions.
- Unrecognized Purchases
Check your purchase history for apps, music, or other content you didn't buy.
You're taking a significant step in securing your iPhone by staying informed about these potential entry points and monitoring your Apple ID. The following section guides you through several tests to know if your iPhone is possibly hacked.
Part 3. Is Your iPhone Hacked? Test These 6 Methods To Find Out
If you're worried that your iPhone may have been hacked, there are a few things you can do to test it. Here are six practical ways to check if your device has fallen victim to a hack.
Check for Unfamiliar Apps
Start by scrolling through your apps. If you spot any you don't remember downloading and that look sketchy, it's time to investigate. Delete any suspicious apps immediately.
Review Your Recent Logins
Go to your Apple ID account settings and review recent logins. Look for any unfamiliar locations or devices that have accessed your account without your knowledge. If something seems off, it's a cause for concern.
Run a Malware Security Scan
A simple way to test if your iPhone is hacked is to install a trusted mobile security app. These apps can scan your phone for malware, spyware, or other malicious software that could compromise privacy.
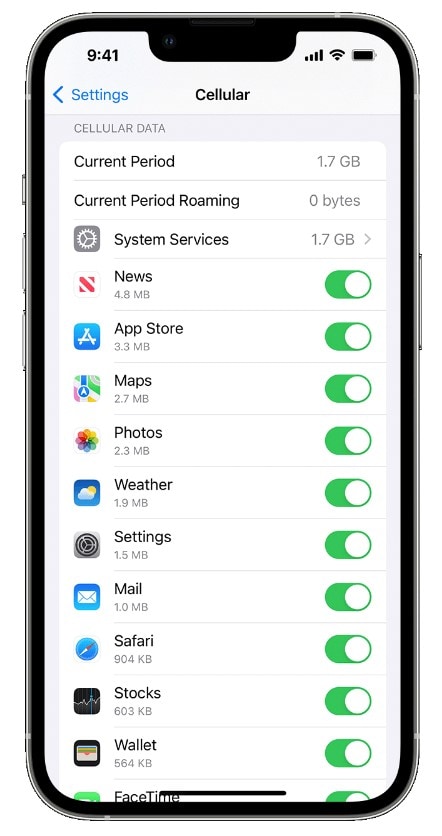
Monitor Your Data Usage
Keep an eye on your data usage. An unexplained increase in data consumption might show that an app is running in the background, sending your data to unauthorized sources. Investigate the cause if you notice excessive data usage.
Check Your Microphone and Camera Settings
Open your iPhone's settings and review which apps can access your microphone and camera. If you see apps that shouldn't have these permissions, disable them immediately. Hacked apps often exploit these features.
Check Your Battery Usage
Examine your battery usage in settings to identify apps consuming an unusual amount of power. If a seemingly innocuous app drains your battery, it might run malicious processes.
If you think your iPhone may have been hacked, it's important to take action to protect your data and privacy. The next section of this article will discuss each of these methods in detail, so keep reading to learn how to test if your iPhone is hacked and what to do.
Part 4: Suspect an iPhone Hack? What To Do Next
If you've run a test and confirmed that your iPhone has been hacked, don't panic. You can do a few things to protect your device and personal information.
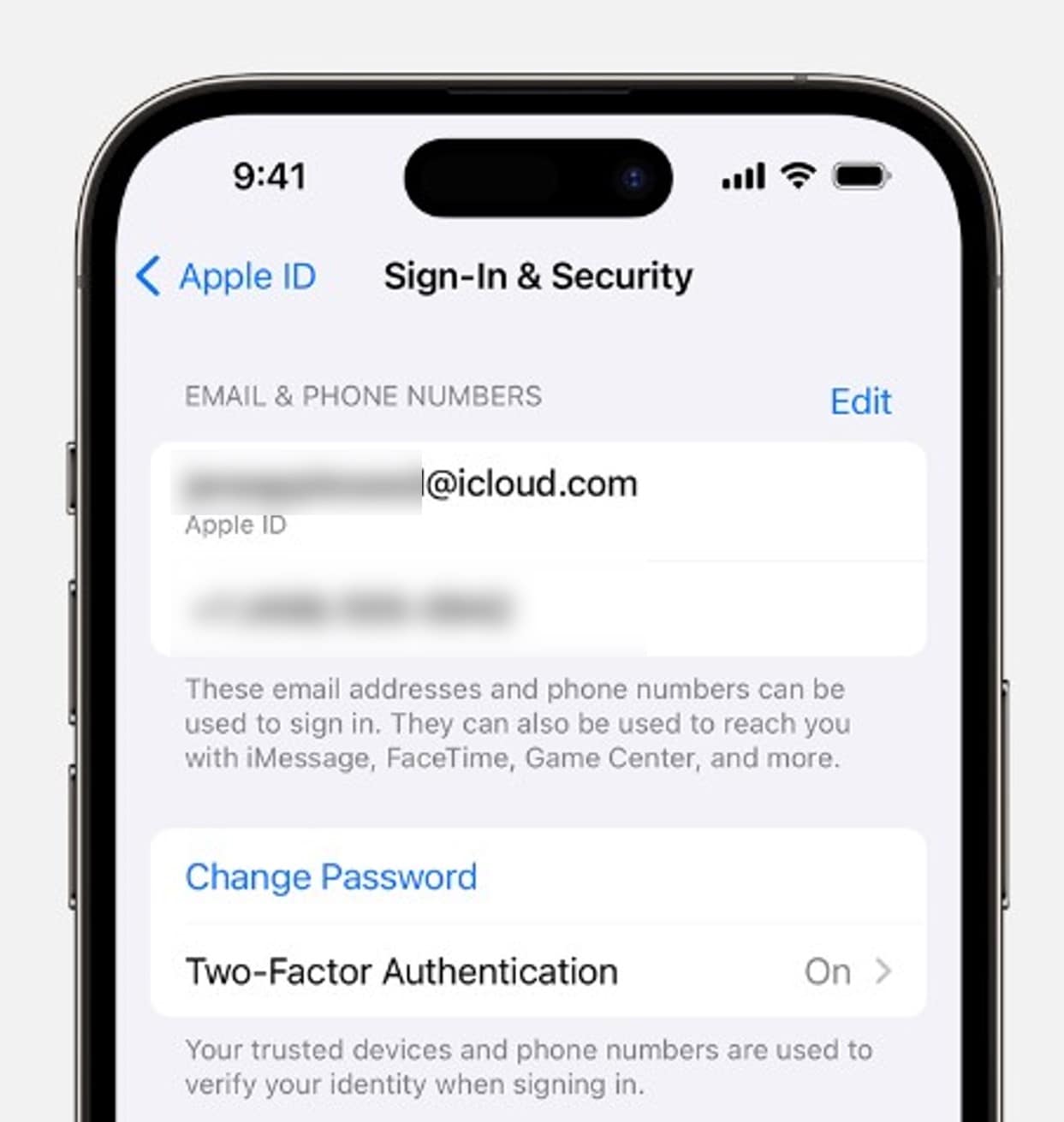
Change Your Apple ID Password
Start by changing your Apple ID password. Ensure it is unique and strong, combining numbers, letters, and special characters. Here's how to do it:
Step 1: Go to Settings > [name] > Sign-In & Security on your iPhone.
Step 2: Tap Change Password, enter your current password, and create a new password.
Step 3: Tap Change Password to confirm the changes.
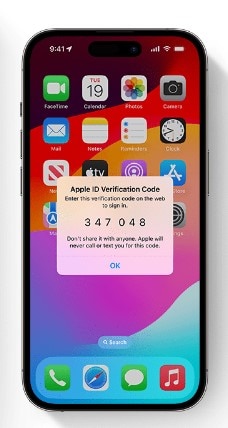
Enable Two-Factor Authentication
Protect your Apple ID from unauthorized access with two-factor authentication. It requires a verification code sent to your trusted device or phone number before anyone can sign in. You'll also need to enable two-factor authentication to use Safety Check on your iPhone. Here's how:
Go to Settings > [name] > Sign-In & Security, tap Turn On Two-Factor Authentication, then Continue. Follow the instructions on the screen to complete the setup.
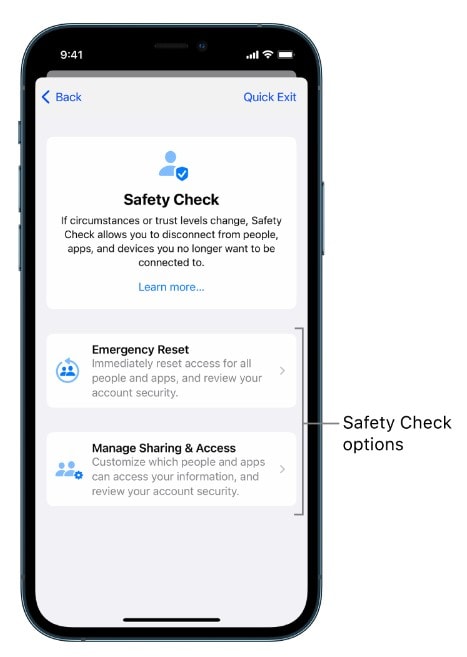
Use Safety Check
Safety Check is a feature in iOS 16 or later that allows you to review and reset sharing and access with people, apps, and devices. Stop sharing your location with everyone, reset app permissions, and sign out of all connected devices. Here is how to access Safety Check to protect your privacy and security:
To access Safety Check on your iPhone, open the Settings app, tap Privacy & Security, then tap Safety Check.
Check Your Apple ID Device List
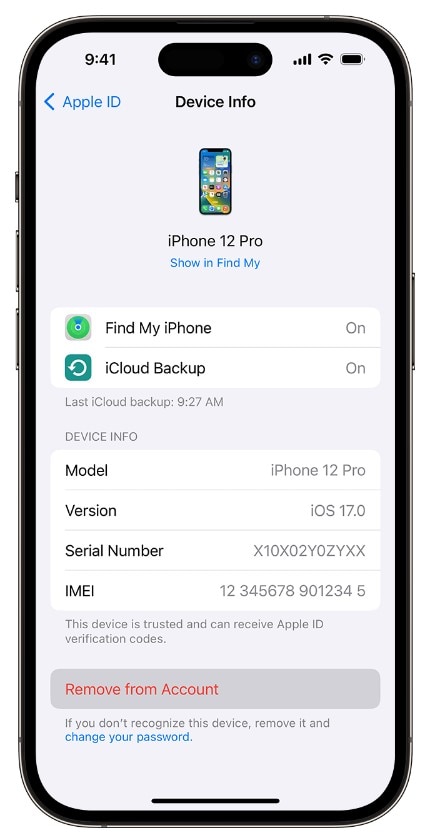
See who's accessing your account. Check your Apple ID device list; If you spot any devices you don't recognize, it's a sign of potential compromise. Remove them immediately. Here's how:
Step 1: Go to Settings > [name] on your iPhone. Scroll down and tap the device name to see if it's trusted.
Step 2: Tap Remove from Account and confirm.
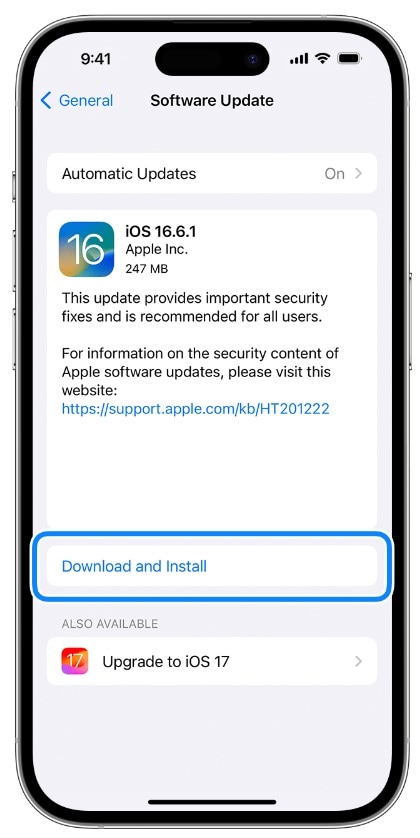
Update Your iOS
Regularly update your iOS to the latest version. Apple continually releases security patches and fixes to address known vulnerabilities. Keeping your device up-to-date is a proactive step in safeguarding your iPhone.
Report to Apple Support
If you strongly suspect your iPhone has been hacked, reporting the issue to Apple Support is crucial. They can provide guidance and support in securing your device and Apple ID.
Confirm if Your iPhone Is Jailbroken
If your iPhone is jailbroken, it's more vulnerable to hacking. That's because jailbreaking removes some of the security features that Apple has put in place to protect your device. By using Wondershare Dr.Fone to check your iPhone's device details, you can see if it's jailbroken and take steps to secure your device if it is.
Part 5: Easy Way To Check if Your iPhone Is Jailbroken
Dr.Fone's iOS device verification feature is a powerful tool for ensuring your device is genuine and has not been tampered with. The report includes "Ex-factory Value" (what it should be) and "Read Value" (what Dr.Fone detects) for each of these test items. Mismatched values indicate potential part replacements. Here are two reports that Dr.Fone can generate for the iPhone verification test:
- Device Details Report
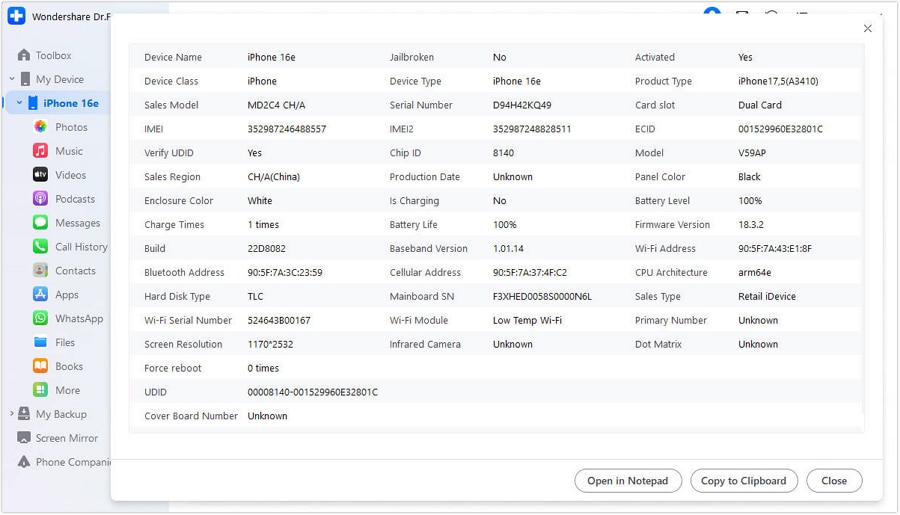
This feature provides a comprehensive snapshot of your iPhone's key details. It includes information like your device's IMEI, jailbreak status, verified UDID, battery life, mainboard serial number, and firmware version.
- Verification Report
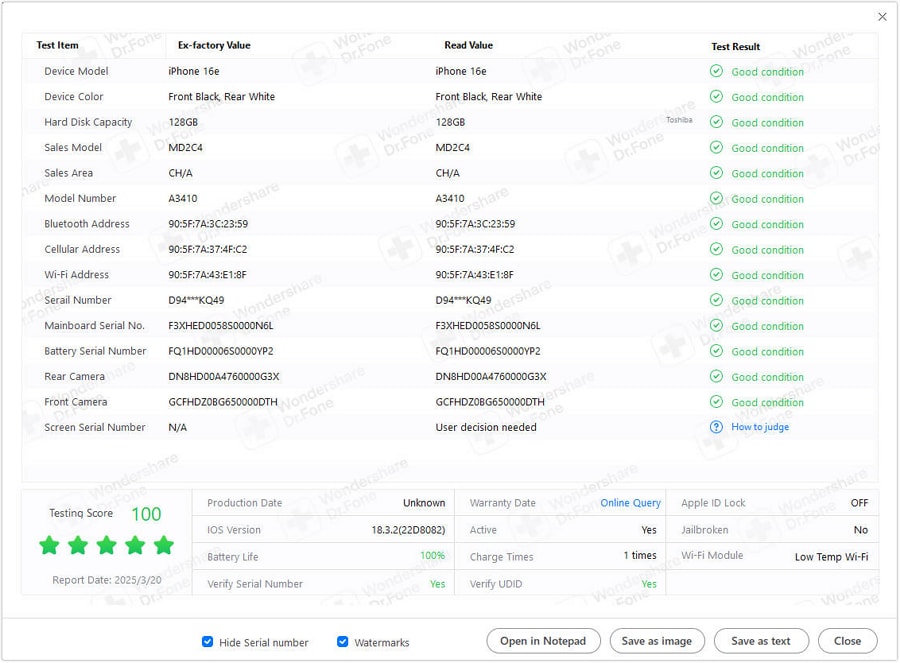
The Verification Report goes further by testing various aspects of your device. It checks your device color, hard disk capacity, battery serial number, Touch ID serial number, and even the status of your rear and front cameras. There is also a testing score after the Apple device verification.
How To Check if Your iPhone Is Jailbroken (Step-by-Step)
Dr.Fone is a user-friendly tool that simplifies checking your iPhone's integrity. No need for technical knowledge – anyone can use it. Get all the details about your device with the Verification Report on Dr.Fone. Here's how:
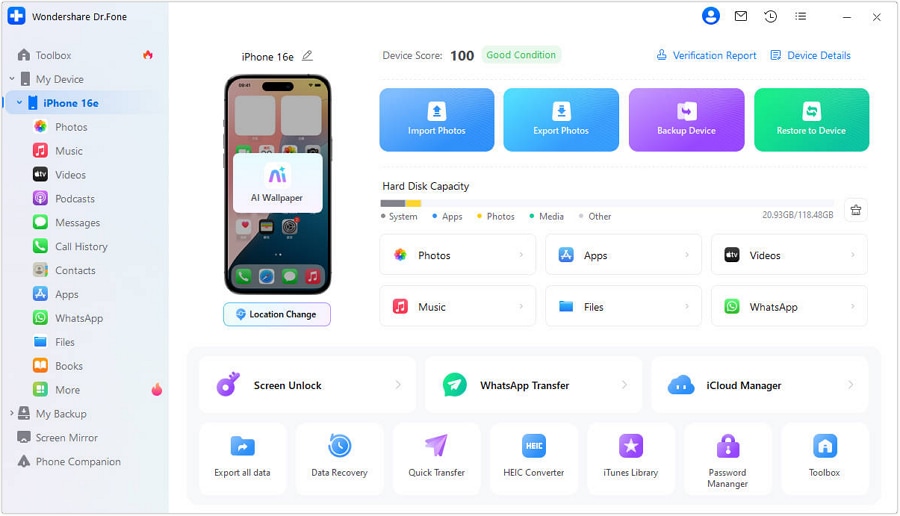
Step 1: Download and install Dr.Fone on your desktop computer, then launch the application.
Step 2: Go to My Device from the left-side navigation pane. Follow the on-screen instructions to connect your iPhone to your desktop via USB cable or wirelessly.
Step 3: Select your iPhone device name from the My Device list. You will now see your iPhone details overview, including your Device Score and Jailbroken status. Click Device Details in the upper-right side to see more information about your iPhone, such as the number of force reboots and charge times.
Step 4: Click Verification Report on the upper-right side for a comprehensive view of your device details and condition.
Conclusion
In today's digital world, your phones are your lifelines. They store your data, financial information, and most precious memories. That's why it's so important to protect them from hackers. There are different ways to do this, but the most important is regularly testing your iPhone for signs of hacking. You can do it using a security app, checking your phone's settings, and more.
Don't wait until you're left wondering, "Is my iPhone hacked?" Dr.Fone can help you verify your Apple products' authenticity and ensure they are working properly. The tool is especially vital to buy a used Apple product for the first time.
Dr.Fone Basic:
Better Control for Your Phone
Manage, transfer, back up, restore, and mirror your device
iPhone Tips
- iPhone News
- iPhone Activate
- iPhone Data Manage
- 1. Export Notes from iPhone to PC/Mac
- 2. iPhone Notes Duplicate
- 3. Print WhatsApp Messages on iPhone
- iPhone Diagnostics
- 1. Check iPhone Wi-Fi Speed
- 2. Check and Monitor iPhone Temprature
- 3. Put iPhone in Diagnostic Mode
- 4. Test iPhone Screens
- iPhone How-tos
- 1. Force Quit Frozen Apps
- 2. Find Own Phone Number
- 3. Find Blocked Numbers on iPhone
- 4. iPhone Internet Explorer Alternatives
- 5. Sync Thunderbird with iPhone
- 6. Things Can Do with iPhone on Plane
- 7. Tips for Using VLC for iPhone
- 8. iPhone Explorer for Mac and Windows
- 9. Use iPhone as Security Camera
- iPhone Location Tips
- 1. Change iPhone GPS Location
- 2. Hide iPhone/Android Location
- 3. PokeGo++ iPhone
- 4. Change Home Address on iPhone
- 5. See Someone's Location on iPhone
- 6. PGSharp for iPhone
- 7. Change App Store Country
- iPhone Track
- 1. Track iPhone by Phone Number
- 2. Track iPhone without App
- 3. Turn Off Tracking on iPhone
- 4. Spy on iPhone without Jailbreak
- iPhone Tricks
- 1. Unlink iPhones
- 2. Mirror iPhone/iPad to Windows PC
- 3. Turn On iPhone Without Home Button
- 4. Charge iPhone Without Charger
- 5. Free Unlimited Data on Verizon iPhone
- 6. Use iPhone with Broken Home Button
- 7. Use iPhone without Touch Screen
- 8. Remote Control iPhone from PC
- 9. iPhone Stuck on Apple Logo
- 10. DFU Tools for iPhone
- 11. iPhone/iTunes Error 4013
- 12. iPhone Front Camera Not Working
- 13. Download Songs on iPhone/iPod
- 14. Unlock iPhone without Passcode
- 15. Reset iPhone Without Apple ID
- 16. Transfer Photo from Android to iOS
- Find My iPhone Tips

















James Davis
staff Editor